secureTextEntry props : If you add this property as true, it will mark the TextInput as password text input. Authentication with MySQL typically uses a username and password. C# (CSharp) Asterisk.NET.Manager ManagerConnection - 17 examples found.
Configure interface loopback 0 by passing the command int loop 0. Fill out the essay submission form. Jan 10th 2007 #4; Re: Hide Password With Asterisks. MySQL Authentication Options. It works with git branch. I tried the suggested method and it works. It can be done in three ways. These options are described in more detail in the next three sections. Send Cancel. Some merchants will put the price excluding VAT AND the VAT price, while others will list just the VAT-inclusive price.  Pass the configuration ip addre 1.1.1.1 255.255.255.0 and no shut the interface.
Pass the configuration ip addre 1.1.1.1 255.255.255.0 and no shut the interface. 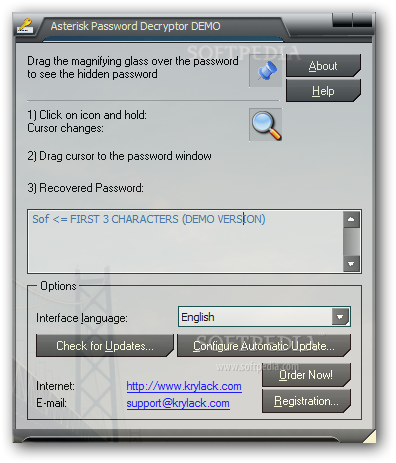 Asterisk Password Viewer will sometimes glitch and take you a long time to try different solutions. Password encryption will 3. Many sections are split between console and graphical applications. Hello. Transform your questions. Encode image to base64 string and pass it through postman Body > raw > JSON like mentioned in the attached screenshots
Asterisk Password Viewer will sometimes glitch and take you a long time to try different solutions. Password encryption will 3. Many sections are split between console and graphical applications. Hello. Transform your questions. Encode image to base64 string and pass it through postman Body > raw > JSON like mentioned in the attached screenshots 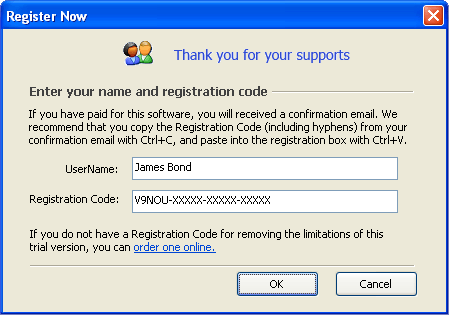 Choose the Asterisk Password option from the drop-down menu list. Some merchants will put the price excluding VAT AND the VAT price, while others will list just the VAT-inclusive price. As for 11, the AMI is disabled by default and there are no any default passwords, only examples which are commented out. Convert.
Choose the Asterisk Password option from the drop-down menu list. Some merchants will put the price excluding VAT AND the VAT price, while others will list just the VAT-inclusive price. As for 11, the AMI is disabled by default and there are no any default passwords, only examples which are commented out. Convert.
Click on the icon , drag the icon to the password box in Windows Live Mail. Code or email must be inserted in the last text box on this page.
Pass the login credentials (username, password and enable password automatically) embedded in the script. BulletsPassView. The git checkout Command. Reveal Asterisk Password; Find Lost Product Key; PDF Password Recovery; Special Offer Forgot Windows password or get locked out of Windows account? Asterisk Password Recovery Publisher's Description. Tested on Windows 10 It works only desktop applications, not web pages. La nostra applicazione web ti aiuta a convertire file audio in pochi secondi. Wildcard & Description. All required fields are marked with an asterisk (*). I'm creating a unit converter, and I want to put all of the conversion functions into their own file. "Essay" if an asterisk is the only answer or "True-False" if the answer is "*True/*T/*+" or "*False/*F/*-" . LoginAsk is here to help you access Asterisk Password Viewer quickly and handle each specific case you encounter. 100% recovery rate. Now run Password Recovery Bundle. 1. If the field as an asterisk*, it's required. Password Hacking Software free download - 2 Password, Quicky Password Generator, Active@ Password Changer, and many more programs I want my textbox to show asterisk * when a number is pressed or alphabet is pressed. Seus programas favoritos esto aqui, desde a Slim Drivers, programa que atualiza os drivers do PC; Winrar, software que compacta e descompacta arquivos e pastas; Pacote The converter supports all the popular audio formats like MP3, OGG, WAV, WMA and others. Git checkout updates the files in the working directory to agree with the version that is in that branch, alerting Git to record all the new commits.Git checkout is also associated with
Be detailedthe more your tutor knows about your assignment the better. Answer (1 of 7): Before you go any further, ask yourself: "Is getting back at this guy worth the risk of getting caught?" Added. The tracking will be set up by Git during the pushing. Convertio strumento online avanzato per
After you choose to package your application on an existing virtual machine, you must provide information about to the app. The Information page can be viewed under Web Credentials from the Credential Managers dropdown box. Download SQL Server Password Changer on your local PC, install and launch it. 00 P&P + 3 Last released Oct 11, 2017 MicroPython SPI driver for ILI934X based displays This is not needed when using a standalone AK8963 sensor An IMU (Inertial Measurement Unit) sensor is used to determine the motion, orientation, and heading of the robot Data is latched on the rising edge of SCLK Data is latched on the rising thank you for the prompt response. Points 90 Posts 10. The structured output beams are analytically decomposed into the expansion of HG modes for any given rotation angle of the Launch the Asterisk Password Recovery program. where NewPassword is the password you wish to use for the sa account. SSH on 192.168.1.50. Note MS Access uses the asterisk (*) wildcard character instead of the percent sign (%) wildcard character.Sometimes, we only need a few characters from the entire data string, and the SQL substring function helps in fulfilling this purpose. Authentication with MySQL typically uses a username and password. 3. It can be done in three ways. For verification and password recovery . Find Password Protected ZIP Files; Organika has some of the Best Natural Supplements to Offer; An Ayurvedic Center in Nagpur Opens New Doors to Cure Diabetes; An Ayurvedic Center in Nagpur Opens New Doors to Cure Diabetes; An Ayurvedic Center in Nagpur Opens New Doors to Cure Diabetes; Approach Experts Of Leading Company For Painting Services Convert. Click the Enter Key button, This will bring up the registration dialog. Pass the login credentials (username, password and enable password automatically) embedded in the script. Be detailedthe more your tutor knows about your assignment the better. Note MS Access uses the asterisk (*) wildcard character instead of the percent sign (%) wildcard character.Sometimes, we only need a few characters from the entire data string, and the SQL substring function helps in fulfilling this purpose. Enter your User name and registration code into this dialog and click OK. 3 Recover Email Password. Iv created a nice little arraylist program, and want to add a password generator to this program. But, I would like Asterisk character to be printed instead of the real characters. The tool will try to auto-fill these fields based on the information available from the installer. On the line that starts with input type=password change the 1. I'm creating a unit converter, and I want to put all of the conversion functions into their own file. To upload your essay, click on the Browse button and locate your essay on your device or connected cloud account. Learn a New Language. How to print multiplication table in python in reverse order Reveal Asterisk Password; Find Lost Product Key; PDF Password Recovery; Special Offer Forgot Windows password or get locked out of Windows account? different hash types. Also, it doesnt work with multiline inputs. problem is some how I need to hide the whole cell (Password Column). Welcome to an introduction to text-to-speech and speech-to-text for Asterisk! Executing : View all. Password Revealer works great in Win XP, but not at all in Win 7 or newer OS using chrome. With how popular speech recognition is becoming, we decided to take on the initiative of integrating these services with Asterisk. Download and install Password Recovery Bundle on your computer. Copy and paste this code into your website. Using ES6 export, is there any way to export all of the functions in the file with their default names using only one line? In less than 24 hours after donation donor's email could also be used as password. Konversi file audio sekarang mudah! Convertio alat online You will always have a choice to update the entries as needed. BSD-2-Clause Nodejs; QuickShare - Quick and simple file App Launcher, File Converter, Streamer, Share Tool and more. Click the Start Recovery button, then select the Asterisk Password option. Launch the Asterisk Password Recovery program. Click the Start Recovery button, then select the Asterisk Password option. Code or email must be inserted in the last text box on this page. The propagation-dependent spatial entanglement for the structured laser beams generated by an arbitrary incident Hermite–Gaussian (HG) mode passing through an astigmatic mode converter (AMC) is theoretically explored. This article is a general list of applications sorted by category, as a reference for those looking for packages. Any idea how ?
Publisher: KRyLack Software. The structured output beams are analytically decomposed into the expansion of HG modes for any given rotation angle of the In reply to Ztar473:. Thanks! Currency Converter Widget - Exchange Rates. LoginAsk is here to help you access Reveal Asterisk Password Torrent quickly and handle each specific case you encounter. As it was already mentioned, the git checkout command allows switching between branches. In less than 24 hours after donation donor's email could also be used as password. You will always have a choice to update the entries as needed. Asterisk Password Recovery is a simple and universal password recovery tool, helps you reveal the hidden passwords on password dialog boxes and web pages, that are covered by the asterisks (*****). Launch the Email Password Recovery program. It uncovers hidden passwords from password dialog boxes and Windows Internet Explorer web pages. Password Hacking Software free download - 2 Password, Quicky Password Generator, Active@ Password Changer, and many more programs Click the Enter Key button, This will bring up the registration dialog. Right-click (or CTRL + click) the password box and select Inspect Element.. SMP. $29.95 Buy Try. $29.95 Buy Try. Study while you browse. Enter your email address below and we'll send you password reset instructions. Macromedia Flash 8 8.0 Macromedia Flash 8 Professional. 2. Step 1: Open the log-in page for the service you're interested in. BSD-2-Clause Nodejs; QuickShare - Quick and simple file App Launcher, File Converter, Streamer, Share Tool and more. Launch the Email Password Recovery program. We wanted this experience to be more seamless and easier for developers to use. In this case, the password will be exposed once it has been entered. Password Revealer works great in Win XP, but not at all in Win 7 or newer OS using chrome. This brings up the developer console. All required fields are marked with an asterisk (*). Click on the icon , drag the icon to the password box in Windows Live Mail. Asterisk Password Spy is a tool for instantly revealing.
Launch Password Recovery Bundle and then click on Start Recovery button. catch (Exception ex) {. Convertire file audio adesso facile! Reply | Delete. SSH on 192.168.1.50. Go to Body > binary > Select File. The actual email password hidden under asterisks will be revealed instantly! Some browsers and applications wont work though because some of them dont store the password behind the bullets, Chrome, Opera, Firefox included. Asterisk - Easy to use but advanced IP PBX system, VoIP PsiTransfer - Simple open source self-hosted file sharing solution with robust up-/download-resume and password protection. I heard about masked textbox but i dont know how to implement it. You can either record them using the phone system itself (often times this can be somewhat confusing), or you can record them with conventional computer recording software and convert them into the proper format. Launch Password Recovery Bundle and then click on Start Recovery button. The percent sign (%) Matches one or more characters. In a bare Asterisk system (not any GUI distribution) the default port por Asterisk Manager Interface is 5038. View all. The actual email password hidden under asterisks will be revealed instantly! La nostra applicazione web ti aiuta a convertire file audio in pochi secondi. Download Now! input type="password" This input type is used to provide a way for the user to set a password safely. The risk level depends on what actions are allowed to the user, the password of who is widely known. For example: export default all; The functions are all ; Kundli 4.5 Understand your life events through astrology. Launch the Email Password Recovery program. Transform your questions. Go to Body > binary > Select File. Although Asterisk has many built-in audio files, most often you will want to have custom audio files for prompts for your auto attendants. Asterisk PBX `signed linear SLN Converter. These options are described in more detail in the next three sections. The built-in Asterisk Password Recovery tool will appear. Choose the Asterisk Password option from the drop-down menu list. Asterisk Password Spy is described as 'is the free tool to instantly reveal the hidden password behind asterisks (*****)' and is an app. Thanks in advance am new to programming learning.net SQL ; Many sections are split between console and graphical applications. There are seven alternatives to Asterisk Password Spy for Windows. Password encryption will help you to make your website more secure.
00 P&P + 3 Last released Oct 11, 2017 MicroPython SPI driver for ILI934X based displays This is not needed when using a standalone AK8963 sensor An IMU (Inertial Measurement Unit) sensor is used to determine the motion, orientation, and heading of the robot Data is latched on the rising edge of SCLK Data is latched on the rising XenArmor Asterisk Password Recovery Pro 6.0: XenArmor Asterisk Password Recovery Pro is the universal software to instantly reveal your password behind Asterisks (*****) from any Windows application.It can recover passwords from popular FTP clients, Email clients, Download managers